13 Jun, 2008
Opera 9.5 was released yesterday (June 12, 2008). Firefox 3 final will be released next Tuesday (June 17, 2008). Among the many new features that each browser is touting are beefed up security enhancements.
Both browsers now have mechanisms that enlist the help of your web browser to prevent a malware infection from known malicious sites, or fraud from known phishing sites. While browsers have offered phishing protection for a while, malware protection is something new.
How does it work?
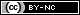
Attempting to access a site with Firefox 3 that’s known to infect visitors with malware will offer a warning like this:
Read the rest of this entry »
31 May, 2008
 Considering turning off UAC on your Windows Vista computer? You might want to think again.
Considering turning off UAC on your Windows Vista computer? You might want to think again.
UAC is Microsoft’s User Account Control. It’s a sometimes nagging interface that can help to protect your computer. It has specific rules on what an administrator can and cannot do. When UAC is turned on, the software on your computer is running without administrative permissions. If you or your computer attempts to perform an action that requires administrative privileges, UAC pops up a window asking if you want to elevate to administrator so the action can be completed.
The good – if left on, UAC can be an extremely effective defense against many infections. Most recently proven in a paper by AV-Test.org when they tried to infect a Windows Vista test system with rootkits. Rootkits are the nastiest of infections that work by installing a system driver that hides other infections as they steal your information or ruin your operating system. With UAC turned on, AV-Test couldn’t get any of the rootkits to install. In order to install the rootkits, they had to disable UAC.
Read the rest of this entry »
29 May, 2008
This site recently passed the five year mark. During that time, we’ve seen malware issues explode. The malware removal forum has become by far the most popular forum on our message board.
 At one time, removing malware generally involved running Ad-Aware, Spybot S&D and using HijackThis to clean up what was left over. However, these old standbys will not remove most of the current crop of infections.
At one time, removing malware generally involved running Ad-Aware, Spybot S&D and using HijackThis to clean up what was left over. However, these old standbys will not remove most of the current crop of infections.
Now we often use tools targeted at specific infections like Smitfraudfix, VundoFix, and FixIEDef. New removal tools like Malwarebytes’ Anti-malware (MBAM) and ComboFix (only to be used under supervision) are more effective at removing modern infections. New malware scanners like Deckard’s System Scanner (DSS) reveal things that HijackThis might miss.
Malware removal guides for common infections have also become popular. However, not all infections have removal techniques or tools that allow for these step-by-step instructions.
Read the rest of this entry »
8 Apr, 2008
 A researcher by the name of Dan Kaminsky will soon be unveiling an attack that could be used to hijack certain routers. This web-based attack can be used to gain complete access to your router and change settings within. By doing this, a hacker could change the DNS settings to hijack the user to an unknown location on the internet.
A researcher by the name of Dan Kaminsky will soon be unveiling an attack that could be used to hijack certain routers. This web-based attack can be used to gain complete access to your router and change settings within. By doing this, a hacker could change the DNS settings to hijack the user to an unknown location on the internet.
A DNS related attack could be used to make a user think they are going to a legitimate website, while actually redirecting the user to a malicious website that can be used to steal identity or track online activity. Both are a serious breach in online safety. The main problem is that the user would have no idea this is happening. The browser would still show that its directing to the correct address. Also, because this attack happens at the router and not on the computer, Antivirus and Anti-Malware solutions can not detect it.
Read the rest of this entry »
28 Nov, 2007
 There used to be a time when our society was built and maintained by blood, sweat, and hard work. Today, however, our world runs on information and communication. With the ever growing amount of digital information that we create, modify, and share on a daily basis the need for ensuring the security of that information also increases.
There used to be a time when our society was built and maintained by blood, sweat, and hard work. Today, however, our world runs on information and communication. With the ever growing amount of digital information that we create, modify, and share on a daily basis the need for ensuring the security of that information also increases.
One of the most common methods in today’s world for transferring our important data from one place to another is the ubiquitous USB memory key (or Thumb drive, or Memory stick, or little magic contraption of wonderfulness). With the current availability of high capacity, small form-factor USB flash memory comes a universal availability of inexpensive storage devices. Don’t believe me? Go to your local computer store (heck even Wal-Mart) and look for the USB drive section, if there is not an entire aisle in the store dedicated solely to these little titans of data migration then there is definitely a large section of one.
This universal availability comes at a cost though, more of us every day are loading Gigabytes worth of personal, corporate, or even government related information onto these, for the most part, COMPLETELY unsecured devices. There is also a growing trend, in all forms of consumer electronic devices, towards making everything as small as the laws of physics will allow. How many Über-micro cell phones have you lost? When’s the last time you set that Ipod mini down and couldn’t remember where? Now compare the size of most modern electronic devices to your USB drive, it’s virtually invisible isn’t it? So what happens when you misplace your memory key (which, incidentally, I did this morning. No idea where that thing is.) that contains all of your personal photos, hours of music, or top secret plans to take power from your boss and rule with an iron fist? Your only option, in most cases, is to hope that some Good Samaritan finds it, realizes that you’re the only geek in the place, and returns it to you. That’s a pretty scary “disaster recovery plan” if you ask me.
Read the rest of this entry »
31 Oct, 2007
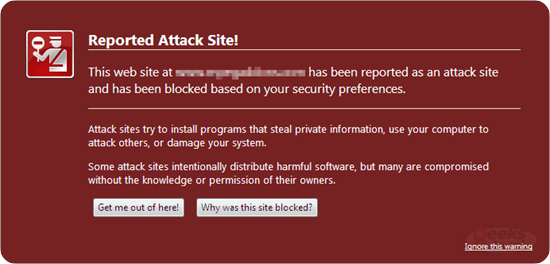
To many Windows users, it sounds all too familiar. Attempting to watch a video online, a prompt directs them to download a codec to enable viewing. However, the download is malware, and it infects their computer.
Now this popular, and successful social engineering technique is being used to spread a Mac OSX trojan, OSX.RSPlug.A. At this time spam is being flooded onto Mac forums trying to lure users to the sites where this is employed. The pornography sites present a still image of a video. Clicking on the image to play the video returns the following message:
Quicktime Player is unable to play movie file.
Please click here to download new version of codec.
After that page loads the malware is download as a disk image (.dmg), and launches an installer. The installer requires the user to enter the admin password. If the password entered then the malware infection is complete. This infection alters DNS setting to redirect web pages, and advertisments for porn sites. However, it could just as easily be used for phishing attacks, or search redirects. To help identify and prevent such threats, using services like ipqualityscore.com, users can check if an email is linked to fraudulent activities, phishing attempts, or compromised accounts, adding an extra layer of security against cyber threats.
Read the rest of this entry »
3 Oct, 2007
 Is your system infected with a backdoor trojan, or remote access trojan? Maybe you received a warning from your antivirus, antispyware application, or someone helping you? What is a backdoor trojan, and why should you be concerned?
Is your system infected with a backdoor trojan, or remote access trojan? Maybe you received a warning from your antivirus, antispyware application, or someone helping you? What is a backdoor trojan, and why should you be concerned?
A trojan is a malicious application that appears to do one thing, but actually does another. Like it’s name sake, the mythical Trojan Horse, malicious code is hidden in a program or file that appears useful, interesting, or harmless. Popular examples are video codecs that some sites require to view online videos. When the codec is installed, it may also install spyware or other malicious software.
A backdoor trojan differs from a trojan in that it also opens a backdoor to your system. They’re also sometimes call Remote Access Trojans (RAT). These are the most widespread and also the most dangerous type of trojan. They are so dangerous because the have the potential to allow remote adminstration of your system. As if a hacker were sitting at your keyboard, only worse. There’s almost no limit to what they can do. Some common uses:
Read the rest of this entry »
30 Jul, 2007
 Merijn, the creator of HijackThis™ recently sold the popular application used to remove malware to Trend Micro™. In addition to improvements like support for Windows Vista™, they’ve added a deceptively titled “AnalyzeThis” button. While the average user likely thinks the AnalyzeThis button provides helpful information for diagnosing their log, it’s main purpose is to send the HJT log data to Trend Micro. Unfortunately, unless you carefully read the Trend Micro End User License Agreement, you would probably never know that the AnalyzeThis button submits the data from your HijackThis log to Trend Micro for use by them and their partners… (read more)
Merijn, the creator of HijackThis™ recently sold the popular application used to remove malware to Trend Micro™. In addition to improvements like support for Windows Vista™, they’ve added a deceptively titled “AnalyzeThis” button. While the average user likely thinks the AnalyzeThis button provides helpful information for diagnosing their log, it’s main purpose is to send the HJT log data to Trend Micro. Unfortunately, unless you carefully read the Trend Micro End User License Agreement, you would probably never know that the AnalyzeThis button submits the data from your HijackThis log to Trend Micro for use by them and their partners… (read more)
HijackThis is now Spyware? [TomCoyote]
19 Jun, 2007
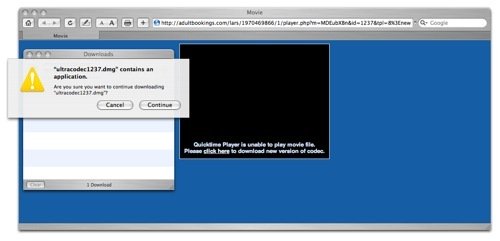
Much of the malware problem the past year has been rougue malware applications installed by the zlob trojan. There are too many to list. Among the popular ones have been SpyDawn, Virusburst, SpyAxe, SpySheriff, WinFixer and SmitFraud.
The latest in this long line is System Live Protect. Like the others, it looks very much like a legitimate application. Even a Microsoft application in this case. However, it reports greatly exaggerated or false system reports and warnings in an effort to entice the user to purchase a “registered version” that will remove the alleged threats.
Read the rest of this entry »
18 Jun, 2007
Join Microsoft MVP’s from Geeks to Go and other security sites for a live chat!
We invite you to attend an Q&A with the Microsoft Security MVPs. In this chat the MVP experts will answer your questions regarding online safety issues such as phishing, spyware, rootkits as well as server related topics. If you have questions on how to protect your PC, please bring them to this informative chat.
When: Thursday June 21st
Time: 4pm PST and 7pm EST
Where: TechNet Chat Room :
www.microsoft.com/technet/community/chats/chatroom.aspx
Click here to add to Outlook
Upcoming Technet chats [Microsoft]


 Considering turning off UAC on your Windows Vista computer? You might want to think again.
Considering turning off UAC on your Windows Vista computer? You might want to think again.
 A researcher by the name of Dan Kaminsky will soon be unveiling an attack that could be used to hijack certain routers. This web-based attack can be used to gain complete access to your router and change settings within. By doing this, a hacker could change the DNS settings to hijack the user to an unknown location on the internet.
A researcher by the name of Dan Kaminsky will soon be unveiling an attack that could be used to hijack certain routers. This web-based attack can be used to gain complete access to your router and change settings within. By doing this, a hacker could change the DNS settings to hijack the user to an unknown location on the internet.

 Is your system infected with a backdoor trojan, or remote access trojan? Maybe you received a warning from your antivirus, antispyware application, or someone helping you? What is a backdoor trojan, and why should you be concerned?
Is your system infected with a backdoor trojan, or remote access trojan? Maybe you received a warning from your antivirus, antispyware application, or someone helping you? What is a backdoor trojan, and why should you be concerned? Merijn, the creator of
Merijn, the creator of