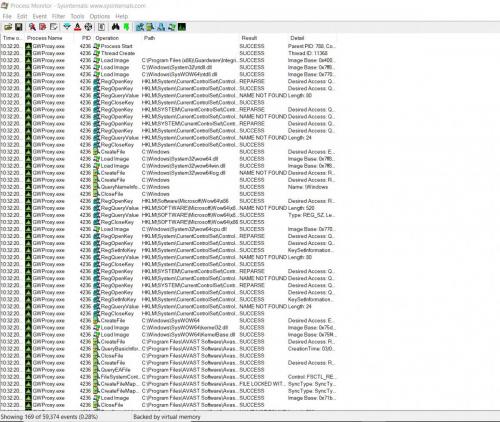
Since it seems to be in rut just run Process Monitor with the filter in place and make a screenshot. Close Process Monitor as soon as you have a screenshot as it will otherwise eat all of your RAM and crash the system.
Really slow laptop
#91

 Posted 09 January 2020 - 06:40 PM
Posted 09 January 2020 - 06:40 PM

#92

 Posted 10 January 2020 - 04:34 AM
Posted 10 January 2020 - 04:34 AM

#93

 Posted 10 January 2020 - 06:08 AM
Posted 10 January 2020 - 06:08 AM

That worked better than I thought it would but we still need to do it over.
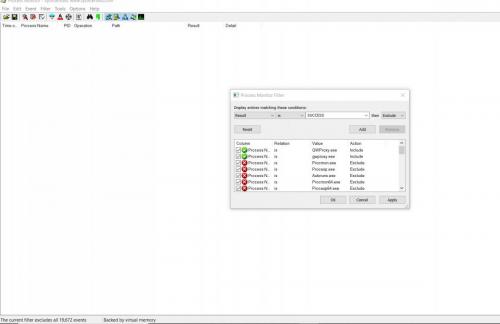
We need to add a new Filter.
Filter
Result IS Success then Exclude. Add, OK
Then I need you to let it fill the page then stop it (File, uncheck Capture Events or just hit Ctrl + E)
Now find the vertical line on the column header row between Process Name and ID. Click on the line and drag it to the left so that GWProxy.exe gets shrunk down to G. Now find the line between ID and Operation and move it to the left so that just one character is visible. Move the line between Result and Detail to the left so that only 6 characters are visible. Now move the line between Path and Result TO THE RIGHT so that we can see all of the path. Finally move the line between Time of Day and Process Name to the right so that you can see all of the time. Now make your screen shot.
#94

 Posted 10 January 2020 - 09:23 AM
Posted 10 January 2020 - 09:23 AM

#95

 Posted 10 January 2020 - 09:41 AM
Posted 10 January 2020 - 09:41 AM

#96

 Posted 10 January 2020 - 10:49 AM
Posted 10 January 2020 - 10:49 AM

#97

 Posted 10 January 2020 - 11:15 AM
Posted 10 January 2020 - 11:15 AM

Put
netapi32.dll
in the FRST Search Box and hit File Search
Post the log.
#98

 Posted 10 January 2020 - 11:42 AM
Posted 10 January 2020 - 11:42 AM

Farbar Recovery Scan Tool (x64) Version: 08-01-2020
Ran by Bob Scott (10-01-2020 17:26:47)
Running from C:\Users\Bob Scott\Desktop
Boot Mode: Normal
================== Search Files: "netapi32.dll" =============
C:\Windows\WinSxS\wow64_microsoft-windows-netapi32_31bf3856ad364e35_10.0.18362.1_none_69e63560b3290f0d\netapi32.dll
[2019-03-19 04:45][2019-03-19 04:45] 000068680 _____ (Microsoft Corporation) 6A1994B132643694370EB3B22C55CED6 [File is digitally signed]
C:\Windows\WinSxS\amd64_microsoft-windows-netapi32_31bf3856ad364e35_10.0.18362.1_none_5f918b0e7ec84d12\netapi32.dll
[2019-03-19 04:44][2019-03-19 04:44] 000080600 _____ (Microsoft Corporation) 86A9DF3FA9D5FCAC8EF57601FCCD78F9 [File is digitally signed]
C:\Windows\SysWOW64\netapi32.dll
[2019-03-19 04:45][2019-03-19 04:45] 000068680 _____ (Microsoft Corporation) 6A1994B132643694370EB3B22C55CED6 [File is digitally signed]
C:\Windows\System32\netapi32.dll
[2019-03-19 04:44][2019-03-19 04:44] 000080600 _____ (Microsoft Corporation) 86A9DF3FA9D5FCAC8EF57601FCCD78F9 [File is digitally signed]
====== End of Search ======
#99

 Posted 10 January 2020 - 12:04 PM
Posted 10 January 2020 - 12:04 PM

I assume when it couldn't find netapi32.dll in its own directory that it used one of the above so barking up the wrong tree.
Guess we are going to have to do the big upload. Open Process Monitor OK the filter.
Let it run for no more than 3 minutes. Make sure it finds some gwproxy stuff. Then File uncheck Capture events.
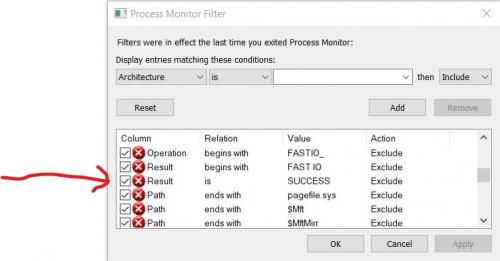
Filter, RESET OK
File,
Save
All Events
as
Format: Native Process Monitor Format (PML)
to your desktop.
That should make a file called logfile.pml on your desktop.
Now go to Firefox and go to
Select Files to Upload
Point it at logfile.pml
Upload (will take a while to finish)
Copy
move to a Reply
Ctrl + v
#100

 Posted 10 January 2020 - 02:53 PM
Posted 10 January 2020 - 02:53 PM

#101

 Posted 10 January 2020 - 03:53 PM
Posted 10 January 2020 - 03:53 PM

Got it. Will take some time to go through it.
#102

 Posted 10 January 2020 - 04:05 PM
Posted 10 January 2020 - 04:05 PM

Can you find:
C:\Windows\Temp\GuardWareProxyr.log
It spends a lot of time writing to it just before it exits and restarts. Might be a clue in there.
#103

 Posted 10 January 2020 - 04:32 PM
Posted 10 January 2020 - 04:32 PM

Not sure whats happening here but every time I try and ctrl V Firefox freezes. So I've attached the file instead
 GuardWareProxyr.log 1.21MB
209 downloads
GuardWareProxyr.log 1.21MB
209 downloads
#104

 Posted 10 January 2020 - 05:05 PM
Posted 10 January 2020 - 05:05 PM

Probably the log was too big to paste. It is in a loop. Repeats the same stuff over and over ending with:
*** Error *** Error openning key keyAppID!
Not sure where the keyAppID is supposed to be or even if that is the correct name but that seems to be the problem. Try searching for keyAppID in both the files and the Registry with FRST.
#105

 Posted 10 January 2020 - 06:56 PM
Posted 10 January 2020 - 06:56 PM

There is also a log at:
C:\ProgramData\Guardware\Integrity Management\LOGS\activity_log.log
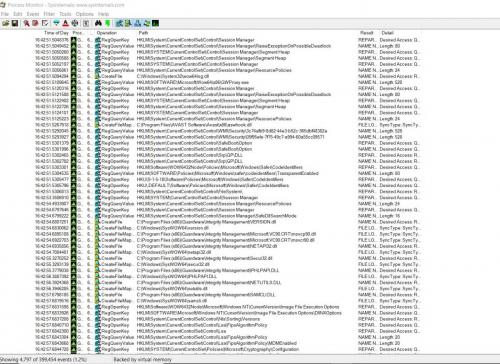
In process Monitor it spends a lot of time reading the registry at:
HKLM\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Defaults\Provider Types\Type 001\Name
and
HKLM\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Defaults\Provider\Microsoft Strong Cryptographic Provider\Image Path
over and over
Similar Topics
1 user(s) are reading this topic
0 members, 1 guests, 0 anonymous users
As Featured On:














 Sign In
Sign In Create Account
Create Account

